Four Password Attack Methods to Open Encrypted File

When you forgot the password for your encrypted file, you may resort to getting a password recovery tool. In the program, you may find there are four password attack methods -- Brute-force, Mask, Dictionary and Smart Attack(Sometimes there are only three methods, excluding Smart Attack). Now we take a wonderful PDF password recovery program -- Cocosenor PDF Password Tuner as an example to elaborate using four password attack methods to open encrypted file.
1. Brute-force
Brute-force refers to the software searches every combination of characters, and/or digits, every possible password, so it may need a long time to find the matched password. However you are allowed to set the search range.
1.1 If you remember the password of the encrypted PDF file just consists of All caps latin(A-Z), you only need to select All caps latin(A-Z).
1.2 If the password just contains small latin(a-z), just select All small latin(a-z).
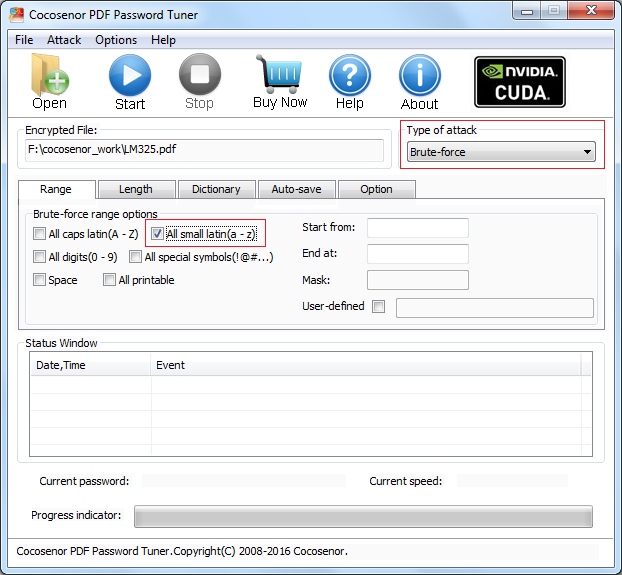
1.3 If the password just includes all digits(0-9), just select All digits(0-9).
1.4 If the password is mixed with caps latin, small latin, digits, special symbols, space and printable, you should select more.
Apart from above three kinds of password, in general, the password is mixed with caps latin, small latin, digits, special symbols, space and printable. For example, your password maybe like John$1988, which includes caps latin, small latin, special symbols, you have to select All caps latin(A-Z), All small latin(a-z), All digits(0-9) and All special symbols(!@#...).
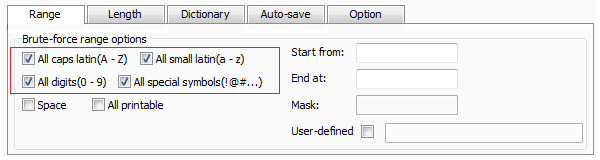
1.5 If you remember the beginning part and/or ending part of the password.
Let's make an hypothesis, the password is John$1988, you remember the beginning parts is John, you can fill "John" in the text area after "Start from". If you can't remember any part except for the last two digits, you can fill "88" in the text area after "End at".
1.6 You are able to set the length of password.
When you select the password type, you can set the minimal and maximal length of password on the Tap of Length. For example, I remember the password of my encrypted PDF file is at least 3 characters, I can make setting as below.
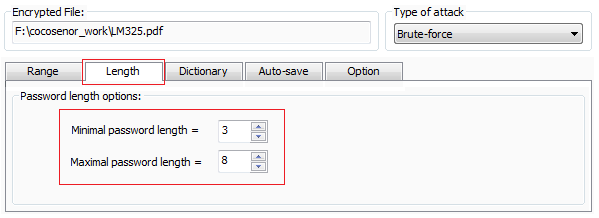
The minimal password length can be as low as 1, the maximal password length can be up to 32.
Tip: The more accurate setting you made, the faster you can open encrypted file.
2. Mask Attack
If you remember some parts of the password, you can select Mask attack. As for Mask attack, please refer to Mask attack - a few minutes to recover a forgotten password is possible.
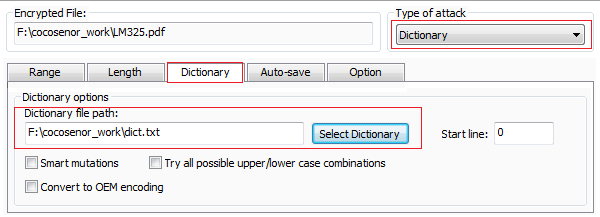
3. Dictionary Attack
A dictionary attack is an attempt to identify your password by a text document, which contains numerous common words, names of loved ones, pets, birth dates, addresses, phone numbers, and some complicated characters combination. The program will scan the text document, but you can also accelerate the password recovery progress by selecting smart mutations, try all possible upper/lower case combinations and Convert to OEM encoding if needed.
Click here, you will learn how to create a powerful dictionary.
4. Smart Attack
Smart attack refers to securing the password through every combinations of possible characters and/or digits, you can't set anything except for the length of the password.
How to Select an Appropriate Attack Type
If you are sure that the password is contained in collection of some characters, you can create a text document, name it as dict.txt, then select Dictionary as attack type, import the text document to the software.
If you just know some parts of the password and the password length, you can select Mask. If you don't know any parts of the password, select Brute-force or Smart.
The difference between Brute-force and Smart is that you can set the range options under Brute-force, but you can't set anything except for the length of the password under Smart.
Sidenote:Once you have selected an appropriate attack method, click the Start button to commence password attack. The password recovery time depends on the complexity of the password. If the password is simple, you can get the password in a second. While the password is complicated, you may get the password in a bit longer time.

